As the email dropped into my inbox, I could see clearly right away it was a phishing attempt, yet my email defenses clearly didn’t agree — at least not right away. Several hours later I would get an alert that the message had been flagged as malicious and was removed. So why, if Microsoft 365 could determine it was malicious hours after being delivered, couldn’t it be flagged as malicious right from the beginning?
The alert posted in the Microsoft 365 console clearly showcased the problem faced by many administrators trying to protect against malicious emails:
Title: Some users were receiving large amounts of spam messages from specific senders in Exchange Online.
User impact: Users were receiving large amounts of spam messages from specific senders in Exchange Online.
More info: This issue only affected a very specific group of organizations, and your tenancy may not have been affected. Mail may have originated from non-legitimate Microsoft domains.
Final status: We’ve confirmed via an extended period of monitoring that the issue has been resolved after the implementation of our fix.
Scope of impact: Some of your users may have received large amounts of spam messages from potentially fraudulent senders in Exchange Online.
Preliminary root cause: Our automated Anti-Spam throttling and blocking services were not properly being triggered due to various reasons in logic. A long-term focus remains on this issue to better understand the cause and methods to address the sources of impact.
Attackers target email relentlessly
Clearly, we cannot depend solely on Microsoft 365 spam filters to protect our networks. Spam filters provided by our vendors are being targeted and there are cases in which they simply do not work. Attackers know that email is an access point into our networks, and they are attacking it relentlessly. Only a combination of end-user education and best practices can reduce the risk of unique phishing attacks.
But they aren’t just limiting themselves to the traditional styles of email attack sequences — now they are using unique ways to enter into our systems. If your IT teams are not using end-user education as a protection tool, you should be seriously looking into adding it. Attackers are pivoting to using emails that correspond to business needs and flows. For example, I am now seeing a rise in quishing — phishing based on QR codes — that is specifically designed to reset two-factor authentication codes.
Attackers know that we are in the process of obtaining new phones and redeploying multifactor applications. The QR codes lead to websites that convince the user to enter their username and password so the attacker can harvest the credentials. The best way to foil them is education — to inform your end users of the exact processes and portals they need to access to reset applications protected by two-factor authentication.
Be aware that when phone vendors release new versions, they increase the communication to your user base. It’s critical to make sure users are aware of the process required to move two-factor applications to a new device with clear, actionable information easily located on your website.
Business action-item phishing
Another, perhaps more insidious style of phishing attacks is the business action item email. These are written as if there are outstanding action items or new business to be done between the user and the bad actor doing the emailing. For example, in the accounting profession, attackers will email to ask the accountants if they are taking on new clientele and request that they accept copies of prior tax returns and tax documents for review. Instead of a link with the tax documents, the attackers send malicious files meant to obtain access to the computer in question in order to gain deeper access to the system.
Again, ensuring that end users know the exact protocol around interacting with potentially new clients and how the firm normally receives new business is the first line of defense against such attacks. For most consulting-style firms, clients are obtained through referrals or connections to another client – that means they are expecting exactly the type of email attackers have learned to spoof. While this process may not be foolproof, it will at least ensure that users are less likely to reach out to these impersonators trying to gain access to our networks.
Password-reset phishing
Next up are malicious emails that try to trick users into completing unnecessary password resets on your email systems in a bid to obtain credentials allowing access to your network. Users should be informed of the exact portal and process needed to reset passwords and other self-serve processes. An internal company IT communication portal can be useful in ensuring that end users know exactly the procedure to follow.
Fake Dropbox and Docusign links are the basis for vendor-specific scams that use stolen graphics from the companies to gain the appearance of authenticity. Creating messages that look very convincingly like they are from vendors we interact with on a daily basis, these emails are yet another attempt to obtain credentials to our networks.
Consider adding two-factor authentication to any site that has a goal of interacting with external clients. Alternatively, consider the policy of only sending and receiving information from sites that are under the control of your firm and not accepting any links from external locations.
Countering the phishing threat on Microsoft 365
Even applying all of these methodologies, attackers know that our weakest link is often the humans that our members of our networks. Humans want to help one another, but that helpful attitude will open us up to attacks.
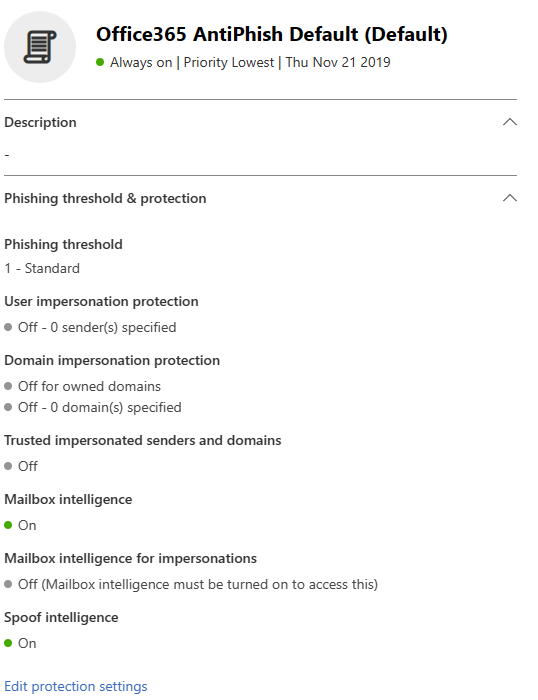
In the case of Microsoft 365, consider either adding or reviewing your settings in Microsoft Defender for Office P2. Specifically, you want to have your team enable impersonation settings in Microsoft 365. For this setting, you can set a maximum of 350 users to be protected by this setting per policy. If you need more than 350 users, you will need to set up multiple policies. While not ideal, this setting should be mandatory for any high-level executive or anyone in a managerial position.
Next, review the phishing levels. Chances are you may have left these settings at the original default. In the case of Microsoft Defender, it’s recommended to set them at 2 or 3.
Microsoft
The default Office 365 settings will let phishing through, so ensure that you review the settings for phishing threshold, user impersonation, and domain impersonation.
As was showcased above, don’t overlook end user education. Even if it’s merely alert emails or discussions about what sort of threats are being seen, ensure your end users are made aware of the risks. Often even if you are fully patched, these phishing attacks can gather credentials and gain access to your network.
If your email protection provides phishing simulations, run these attacks against your network and see how well your human defenses will withstand the typical attacks that are out there. End-user education should not be overlooked or discounted as an effective means to protect your network. With our vendors often failing to protect us, users are often the only thing between our network’s security and an attacker.
Go to Source
Author:
